In today’s cloud-driven workplace, data is constantly being created, shared, and stored across multiple platforms. Without a solid classification strategy, organizations risk losing control over their most sensitive information. Microsoft 365, through the Purview compliance portal, provides a set of powerful tools for discovering, labeling, and governing data across the environment.
Here’s a breakdown of how these features work, their strengths, and the challenges organizations should be aware of.
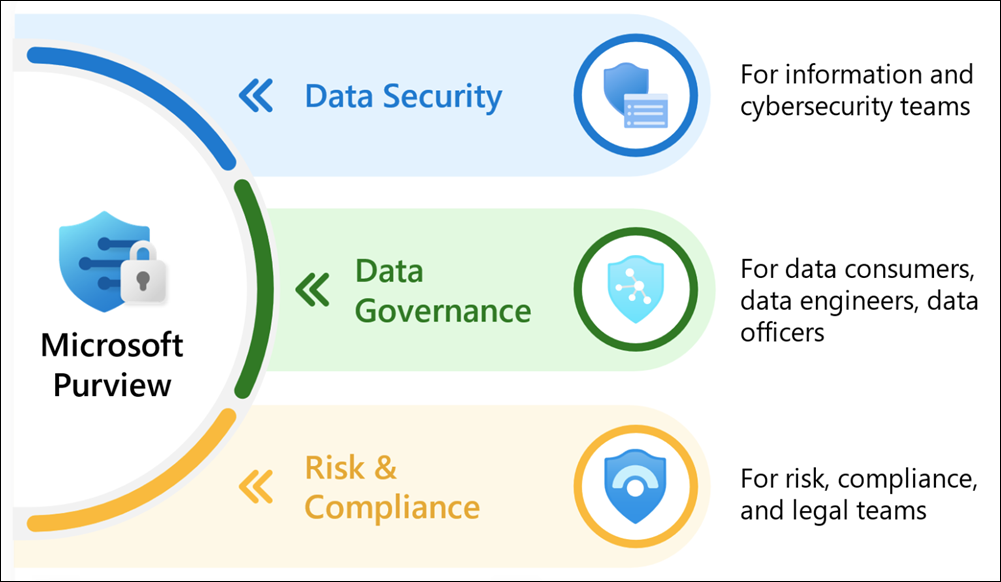
Core Components of Data Classification in Microsoft 365
-
- Discover Before You Enforce
A smart classification strategy begins with visibility. Before rolling out labels and policies, it’s possible to scan your environment to see what data already exists, where it’s stored, and what sensitive information types it contains. This “zero-impact discovery” gives you a baseline without disrupting users. - Labeling Framework
-
- Sensitivity Labels: Used to tag content based on its confidentiality. Labels can automatically enforce encryption, restrict sharing, or add visual markings like watermarks and headers.
- Retention Labels: Control how long data is retained and when it should be deleted. This supports compliance with regulations and internal governance policies.
- Trainable Classifiers: AI-based models that identify content categories such as source code, resumes, or customer feedback, beyond just keywords or patterns.
- Sensitive Information Types (SITs) & Exact Data Match (EDM):
-
- SITs identify data like credit card numbers or passport IDs using pattern matching.
- EDM takes it further by matching exact values from a reference database, reducing false positives and giving more accuracy.
-
-
- Content Explorer
Offers granular visibility into items that contain sensitive information or labels. Admins can drill into locations like SharePoint, OneDrive, and Exchange, view metadata, and understand how data is distributed. - Activity Explorer
Focuses on user and system activity around sensitive data — for example, when labels are applied, removed, or changed. This helps security and compliance teams spot trends and refine policies. - Insights & Dashboards
The Purview portal provides clear dashboards showing top sensitive information types, the most commonly applied labels, and where sensitive data resides. These insights support both compliance reporting and security investigations. - Building a Label Taxonomy
-
- Simple Environments: A straightforward 1-to-1 mapping (e.g., “Public,” “Internal,” “Confidential”) may be enough.
- Complex Environments: Global organizations often face regional legal variations, requiring a more nuanced approach. In these cases, piloting, feedback, and iteration are essential to avoid confusion and misclassification.
-
- Discover Before You Enforce
Why This Approach Works
-
- Visibility First: By understanding the data landscape before applying controls, organizations reduce the risk of user friction and misaligned policies.
- Flexibility: Combining SITs, EDM, and trainable classifiers gives broad coverage for structured, semi-structured, and unstructured data.
- Continuous Feedback: Content Explorer, Activity Explorer, and dashboards make classification an ongoing, adaptive process rather than a one-time project.
- Built-In Enforcement: Sensitivity and retention labels don’t just tag data — they actively control access, protect content, and manage its lifecycle.
Common Challenges
-
- Ambiguous Labels
Users can misinterpret labels if they aren’t clearly defined. For example, a label like “Personal” might mean “personal information” to some and “private use” to others. - Accuracy Issues
Pattern-based SITs can generate false positives. EDM improves accuracy but requires effort to maintain reference databases. - User Adoption
If users see classification as a burden, they may ignore or bypass it. Proper training, simple naming, and piloting are essential. - Regulatory Complexity
Multinational organizations must balance different definitions of “sensitive” across jurisdictions, making taxonomy design more challenging. - Ongoing Maintenance
Classification is never “done.” New regulations, business processes, and data types mean that classifiers, SITs, and labels must be updated regularly. - Resource Requirements
Advanced classification may impact licensing, storage, or processing resources — something to factor into planning.
- Ambiguous Labels
Best Practices for Implementation
-
- Start with a pilot project and refine based on feedback.
- Involve stakeholders from legal, compliance, security, and business units early on.
- Use clear, intuitive label names that employees understand.
- Combine multiple classification techniques (SITs, EDM, AI classifiers) for better coverage.
- Monitor continuously with Content Explorer, Activity Explorer, and dashboards.
- Establish a review cycle to keep policies aligned with regulatory changes and evolving business needs.
Data classification in Microsoft 365 is not just about labels — it’s about visibility, governance, and ongoing protection of critical business information. With the right planning, clear taxonomy, and continuous monitoring, organizations can transform compliance from a reactive burden into a proactive security advantage.
Done well, classification reduces risk, supports regulatory compliance, and gives users confidence in how data is handled — all while embedding governance into everyday workflows.


